
CMMC Compliance Consulting, Gap Analysis & Audit Readiness Assessment Services
Be ready to pass your CMMC audit and secure more contracts.
Ideal for organizations wanting to work with the DoD and its third-party suppliers.
Prove You're Secure
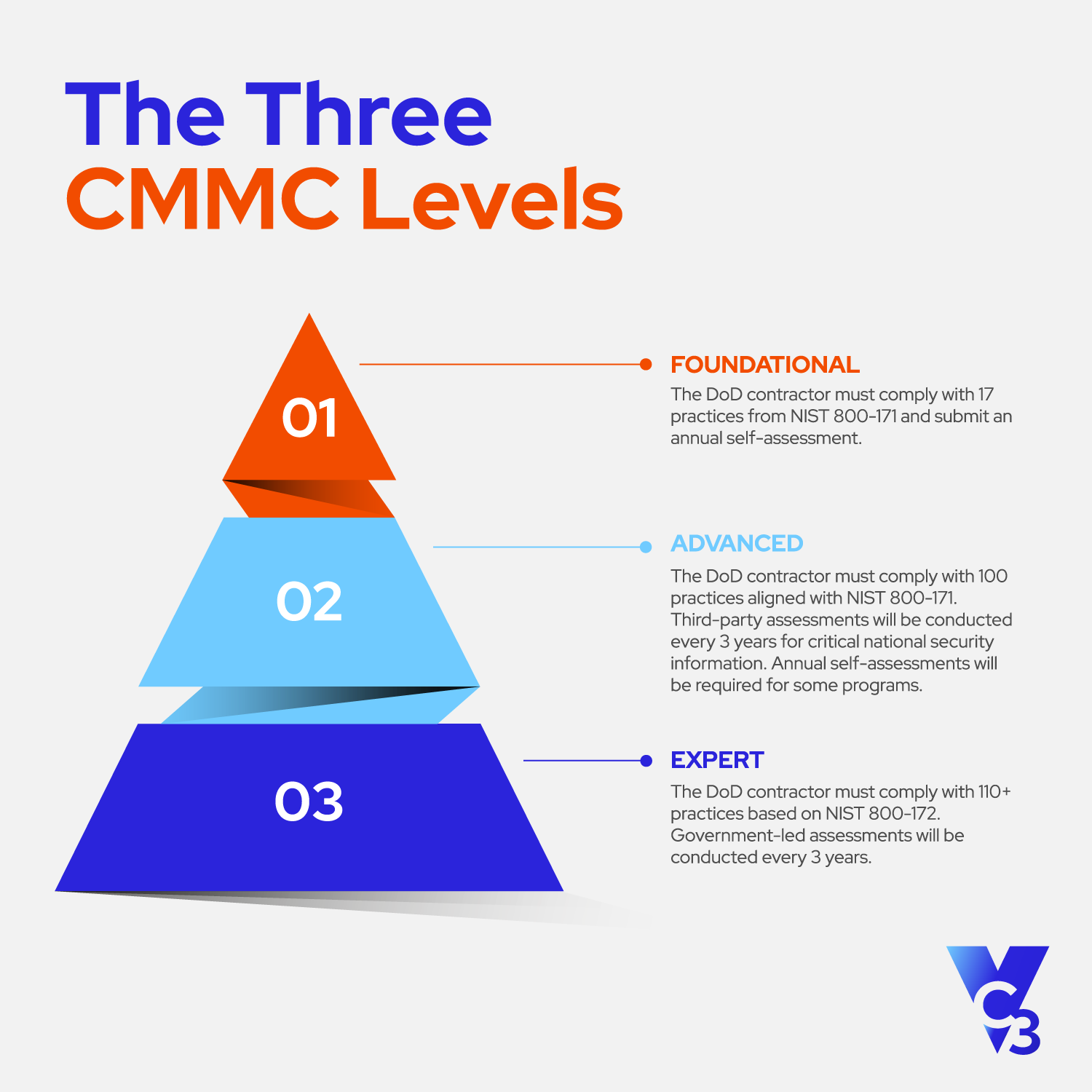
For better or worse, compliance with CMMC is not optional for those in the DoD supply chain. The new certification is part of a continual effort to provide more accurate results, provide more helpful insights, and reveal the best practice for DoD operations.
Keeping and gaining more DoD contracts depends on your ability to verify that you can achieve and maintain the level of security that is required through your DoD contract.
CMMC Consulting for Successful Compliance
VC3 is a CMMC Registered Provider Organization (RPO), ready to help your company prepare for your CMMC audit. Our Registered Practitioners will work with you to create a path to successful compliance.
-
Gap Analysis and Recommendations
Evaluate security measures to determine current security status and provide recommendations for remediation options. -
Remediation and Audit Preparation
Guidance for planning and implementation of technical and non-technical controls to fulfill compliance requirements and successfully pass your third-party audit. -
Ongoing Cybersecurity Management
Augment your IT department with experts who will oversee security operations for CMMC compliance or your whole organization.
3-Step CMMC Assessment Process
Compliance assessments require a significant amount of collaboration with your staff because the process will include a review of your non-technical as well as your technical security policies. This means that HR and department heads will need to be involved.
We’ll guide you through a process that has three steps.
-
Step 1: Gap Analysis and Recommendations
Compliance requirements can be difficult to interpret. We’ll walk you through the process, perform a detailed analysis of your current alignment for the level of compliance you need, and provide recommendations for what is needed so you can meet CMMC compliance requirements to pass your third-party audit.
While we can do much of the technical portion of the assessment on our own, this process is highly interactive and requires significant time spent with you to discuss the controls and what’s needed to meet them. We’ll work together to get you where you want to go.
A Gap Analysis will give you the information you need to submit a self-assessment to the DoD. -
Step 2: Remediation Planning and Audit Preparation
With the results of your Gap Analysis in hand, your next step is to plan how you’re going to implement the missing security controls. These controls will include both technical and non-technical measures. That means that you’ll need to involve multiple departments, not just IT. If your staff doesn’t have the expertise and bandwidth to do this, we can help.
There’s no one-size-fits-all solution for how to achieve CMMC compliance.In fact, there may be numerous options that will meet regulations. In addition to providing you with the information you need to make decisions about how you’ll meet CMMC regulations, we can bring you other recommendations that will allow you to reduce the scope of compliance and reduce the costs of your audit.
-
Step 3: Ongoing Cybersecurity Management
Once you achieve CMMC compliance, the controls that you put in place need to be managed. Even if they have an internal IT team, many organizations are outsourcing security because it’s the most efficient way to bring in all of the knowledge, skills, and tools that are needed for advanced security.
How VC3 Can Help Your Organization Prepare For CMMC Compliance
Although it may seem daunting, Cybersecurity Maturity Model Certification (CMMC) does not have to be a strenuous process.
As a CMMC Registered Provider Organization (RPO), we help organizations implement and maintain the controls of CMMC so they can bid on contracts with the Department of Defense and its supply chain. With over 30 years of experience helping companies with compliance requirements, you can expect to be promptly prepared for any CMMC certification level as quickly and painlessly as possible.
The DoD recognizes that security is an utmost concern, and should never be substituted for cost, schedule, or performance. The Department is committed to keeping sensitive data safe and protecting all parties involved in the contract process.
We are committed to getting organizations certified, quickly and efficiently.

VC3 keeps your organization protected and prepared.
1,100+ municipalities and 700+ businesses turn to VC3 to get out of the IT trenches and back to working on what matters.
of Experience Evolving with the Threat Landscape
Average Relationship Tenure
98% of Employees Are Technical
The capacity, skill set, and experience to help you AIM higher.
-
Fast Deployment
A streamlined assessment process that quickly evaluates your organization’s vulnerabilities and security gaps.
-
Customized Approach
Cyber experts who understand your unique organization that requires more than a check-the-box approach that caters to the masses.
-
Practical Innovation + Costs
Right-sized assessments with predictable costs that are tailored to your organization’s unique requirements.
-
Strategic Consulting
Get a forward-thinking partner that helps you evaluate your options, identify vulnerabilities, and stay protected.
-
Actionable Insights + Takeaways
Our easy-to-understand scorecards highlight your organization’s security gaps and ways to bridge them.
-
Decreased Vulnerabilities
Increased security readiness and specific tactics that help you improve your organization’s cybersecurity foundation.
Our approach to technology enables your organization to AIM Higher.
Lots of companies can set up your laptops or manage your infrastructure. In order to contend with today's challenges, you need more than a break-fix vendor with a "24/7" helpdesk ticket to nowhere. You need a proactive partner that stops the issues before they start. That's where VC3 comes in.
Let's talk about how VC3 can help you AIM higher.
Cybersecurity Resources + Insights
CMMC 2.0 Compliance Explained

3 Most Common Advanced Technologies Businesses Need For Their CMMC Remediat...
