.png?width=575&name=VC3-Cybersecurity-IT-Services%201%20(1).png)
Cybersecurity Maturity Model Certification (CMMC) 2.0 Explained
How to Prepare for Successful CMMC 2.0 Compliance
The Cybersecurity Maturity Model Certification (CMMC) is a new requirement for Department of Defense (DoD) contractors. It's how the DoD certifies a contractor's ability to protect the Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) within the supply chain system. A new version of CMMC was released in November 2021.
The new certification is part of an increased effort to promote the adoption of cybersecurity best practices for DoD operations. That way, the whole supply chain can become more successful at repelling and responding to cyber threats.
Cyber war is a war that the Department of Defense fights every day. Strong and sophisticated as their cyber weapons are, the DoD can’t fight this cyberwar on their own. The entryways to the US defense ecosystem spread out to every business that supplies it with the materials and brain power that it needs to design, build, launch, and maintain its activities.
Enemies will stop at nothing to steal away the advantage that the United States wields as a global technology leader. That means if your business is part of the DoD supply chain, you have been called into service to protect the government data that you store and transmit.
In this guide, you'll learn:
Short on Time? Download the PDF! 👇

1. DoD Suppliers Are Accountable for Cybersecurity
The DoD depends on external suppliers and contractors for a wide array of tasks and projects. During the process, the DoD and contractors exchange sensitive data, which must be protected. Inadequate data safety measures have resulted in significant homeland security risks that have put our military members in jeopardy. CMMC replaces self-certification of compliance with NIST SP 800-171, not because the NIST standards were ineffective, but because self-certification didn’t work.
Under DFARS and DoD rules and policies, the DoD has implemented cybersecurity controls for both contractor and subcontractor levels to protect Controlled Unclassified Data (CUD) that is transmitted, stored, or processed. If a contractor or subcontractor ultimately fails to comply and maintain compliance with the guidelines, they will be unable to bid for DoD contracts.
Security Is Now Equally as Important as Cost, Delivery, and Quality for DoD Vendors
Going forward, cybersecurity will be equally as important as cost, schedule and performance for companies that want to keep and gain more DoD contracts.
The CMMC has been in effect since January 21, 2020 and revised in November 2021. While third-party audit requirements have been changed in CMMC 2.0, contractors should not delay getting started on their path to compliance. Voluntary audits begin in 2022 and companies will need to demonstrate that they’re making progress towards full CMMC compliance at the appropriate level.
So, it is ideal for contractors to get certified as soon as possible.
We’ve created this resource to help you navigate through your CMMC journey.
2. What is the CMMC 2.0?
Cybersecurity Maturity Model Certification (CMMC) is how contractors will communicate and verify cybersecurity standards.
Compliance is designed to completely protect all points in the Defense Industrial Base (DIB). Three levels of CMMC compliance measure and assess cybersecurity practices and processes, certifying a contractor's ability to protect the Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) within the supply chain system.
Each CMMC level builds on the previous level and includes both technical and non-technical requirements. While self-assessment or successful third-party audits are steps in the compliance process, the ultimate goal of CMMC is to enable organizations to meet new threats as they evolve so that organizations never let down their guard.
The CMMC builds upon previous requirements outlined in:
- NIST SP 800-53
- NIST SP 800-171
- DFARS 252.204-7012
- AIA NAS9933
How Far Down the DoD Supply Chain Does CMMC Stretch?
The DoD has implemented cybersecurity controls through CMMC for both contractor and subcontractor levels. Your contract will specify the CMMC level that you will need to achieve and maintain, as well as the data that needs to be protected.
Most companies will need Level 2. (See diagram below.)
Your entire organization does not need to comply with CMMC if you have other customers outside of the DoD. In fact, limiting compliance to just the part of your network and organization that handles FCI and CUI will help you to limit costs when it comes to the actual audit.
What Does CMMC “Maturity” Mean?
In the IT world, we use the word “maturity” to describe how well an organization’s technology is being used to meet business objectives and keep operations running smoothly and efficiently. The lowest level can be described as chaotic with the highest described as strategic. The levels build on each other.
When combined with cybersecurity, maturity denotes increasing capability to manage cyber risks. CMMC levels go from basic to advanced. You can see in the diagram below how the levels build on each other.
3. The Three CMMC Levels Are as Follows:
CMMC 1.0 consisted of 5 levels. CMMC 2.0 has been simplified and condensed to 3 levels.
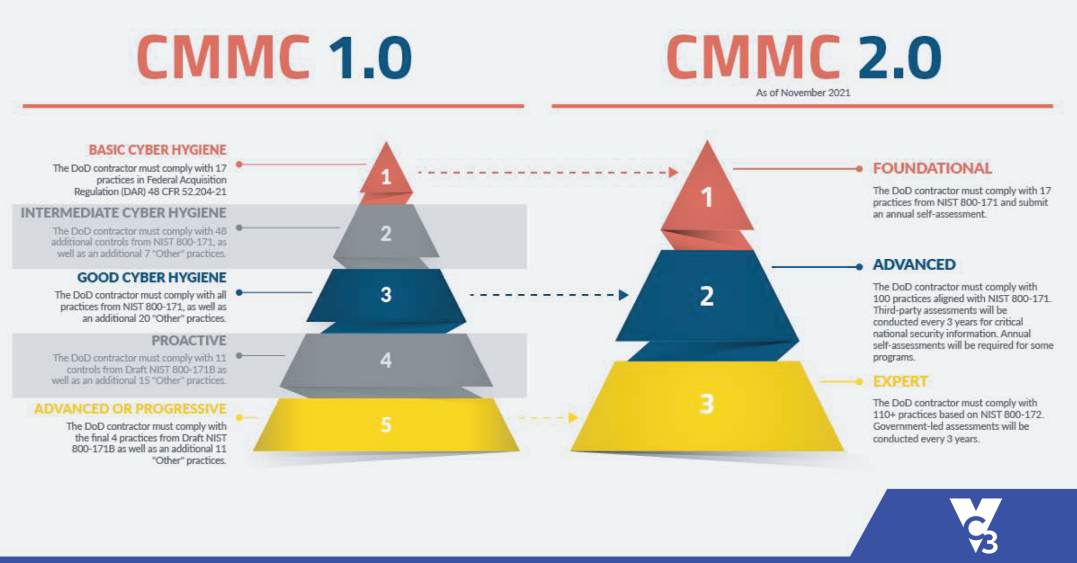
Level 1: Foundational
The DoD contractor must comply with 17 controls from NIST 800-171 and submit an annual self-assessment.
Level 2: Advanced
The DoD contractor must comply with 100 practices aligned with NIST 800-171. Third-party assessments will be conducted every 3 years for critical national security information. Annual self-assessments will be required for some programs.
Level 3: Expert
The DoD contractor must comply with 110+ practices based on NIST 800-172. Government-led assessments will be conducted every 3 years.
4. What is the CMMC Assessment Process?
CUI Discovery
What Data Are You Protecting?
In order to protect Controlled Unclassified Information, you need to determine exactly where it’s stored and how it’s transmitted. Simple as it sounds, this step is tripping up many companies because they can’t identify the information in the first place, or they don’t know where it resides in their network.
Controlled data includes things like contract information, names, PO numbers, technical data, and the like. Your contract should tell you exactly what information you need to protect. If this is not clear, ask for clarification.
Once you identify the data, you can set the scope for compliance. While it’s not a bad thing to increase the cybersecurity stature for your whole organization, you can save costs on your CMMC audit and ongoing management of compliance when you can focus CMMC activities on just the DoD controlled data.
Remediation Plan
Your Action Plan to Prepare for Your Audit
A remediation plan is your task list to prepare for your self-assessment or third-party audit. Don’t expect this task list to be a shopping list of hardware and software that you need to buy.
In fact, many companies don’t need to purchase any additional equipment to prepare for CMMC compliance.
Security controls are both technical and non-technical barriers to network intrusions. Practices and processes associated with the controls detail exactly how controls are implemented.
For example, to identify and authenticate users, you may have Multi-Factor Authorization set up which is a technical control. You also could have a policy (non-technical) that prohibits employees from using the same password for different accounts. Practices and processes detail how these two controls are going to be implemented and managed.
🔎 Related: 3 Most Common Advanced Technologies Businesses Need For Their CMMC Remediation Plan
Gap Analysis
How Are You Protecting the Data Today?
Whether you complete this step through a self-assessment or engage a CMMC consultant for a facilitated assessment, you need to determine where you’re strong and where you have gaps in security practices and processes. What happens with the gap analysis is that you go through all of the required controls and you give them each a yes or a no.
Most businesses that are down a few tiers in the supply chain will ultimately need to meet Level 2 (formerly Level 3 in CMMC 1.0) requirements. At Level 2, you need to have the controls in place, they need to be documented, and you need to provide two evidences for it.
The gap analysis will tell you exactly what you need to do to meet the requirements. You’ll use this information to create a remediation plan. If you need to submit a self-assessment, a gap analysis will meet that requirement.
🔎 Related: CMMC Gap Analysis FAQs
Yes – The Control Is in Place
If your gap analysis found that you already have the security control in place, your remediation plan will indicate if you need to document it and provide the evidences for it.
No – The Control Is Not in Place
When a control is not present, the remediation plan will include a recommendation for adding it, documenting it, and supporting it with evidences.
In addition to security controls, your remediation plan may include suggestions on how you can limit the scope of compliance by segmenting your network and confining compliance to those operations and people who are fulfilling the DoD contract.
Preparing for Your CMMC Audit
Once you have your remediation plan, your job is to make your way through your list and add the controls that are missing, document them, and decide on what evidence you’ll use for verification. Timing is important because you need to be able to show that controls have been in place for a while. You can’t do that if you wait until the last minute.
For CMMC Level 2, you’ll need to prepare two evidences for each control.
For example, an access control policy might have a screenshot of a technical policy in place on the server, and the second evidence could be an interview with an employee responsible for enforcing that policy.
🔎 Related: Writing CMMC Security Policies: The CMMC Compliance Task That Nobody Wants to Do
CMMC Assessment Guidelines: What to Expect When It’s Time for Your Audit
Whether you’re self-assessing or preparing for a third-party audit, you’ll need to define the scope of the assessment.
Limiting where Controlled Unclassified Information is stored, how it’s transmitted, and who handles it will give you less territory to cover. If you need a third-party audit, you’ll save on assessment costs.
CMMC Self-Assessment
For a self-assessment, you’ll submit a spreadsheet that documents two security controls that you’re utilizing to meet the requirement. The controls you choose will depend upon your specific IT environment and your business processes.
As CMMC 2.0 is rolled out, contractors may submit a Plan of Action and Milestones (POAM) as a demonstration that the company is moving towards full compliance. What’s important is that the company can show that progress in cybersecurity maturity is being made.
CMMC Third-Party Assessment
During a third-party assessment, the Assessor will be looking at specific Assessment Objectives that will have a set of determination statements. Determination statements are a set of parameters that explain the performance or function of the objective. In other words, these tell the Assessor what they’re looking for to determine how effective the control is.
Each Assessment Objective will have assessment objects. These are the evidences that you prepared beforehand. They can include documentation, mechanisms deployed by hardware and software, activities, and behaviors.
The methods that the Assessor uses to verify each assessment object will require access to your systems, people, documentation, and facility. Methods will include a combination of:
- Examining – Looking to see if an assessment object is in place.
- Interviewing – Talking to people about the behaviors they use when handling CUI.
- Testing – Triggering or demonstration of a control to see how it responds.
The Assessor will determine if each control is MET, NOT MET or NOT APPLICABLE.
When you’ve done the work to prepare for your CMMC Assessment, you shouldn’t need to worry about the outcome. In fact, the security posture for your whole organization may mature as a result.
How Much Do CMMC Audits Cost?
The cost of your audit will depend on the CMMC Level for which you’re being assessed, the complexity of your network, and other factors that can increase or decrease the time it takes to complete an audit.
Once attained, your certificate is valid for three years with ongoing management.
5. Staying CMMC Compliant
If you’re new to regulatory compliance, you might think that once you’ve passed your audit you can relax. However, compliance – and cybersecurity – is an ongoing process that has to be managed. As with anything, managing compliance takes resources.
The DoD supply chain is extremely diverse, made of up large companies that have their own IT departments to small businesses that utilize a local IT provider. No matter the size, companies can benefit from the services of an MSSP (Managed Security Services Provider) to bring them the knowledge and tools that are needed to efficiently manage cybersecurity and CMMC compliance.
MSSPs can augment your in-house resources and act as an extension of your team. Because they bring advanced tools and extensive knowledge of cybersecurity to your company, you’ll find that you’re not only able to attain CMMC compliance, but you can become better at managing your overall cyber risk.
Whether you rely on in-house or outsourced cybersecurity expertise, the objective is not just to maintain compliance but to know how to respond to possible intrusions and keep up with evolving threats.
🔎 Related: IT Managers: How to Tell Your Boss You Need a CMMC Consultant.
6. Registered Practitioners: Your CMMC Guides to CMMC Compliance
The DoD understands that businesses are going to need some help in preparing for and passing CMMC audits. Through the CMMC Accreditation Body, programs have been created to train individuals and organizations to provide CMMC consulting.

Registered Provider Organization (RPO)
Registered Provider Organizations (RPO) are companies that have at least one trained CMMC consultant (RP) who can work with businesses to prepare for CMMC audits. RPOs have passed an organizational background check and have agreed to the CMMC Accreditation Body code of conduct. They also demonstrate skill in CMMC awareness as part of IT service delivery.

Registered Practitioner (RP)
Registered Practitioners (RP) are consultants who are trained in CMMC methodology and have agreed to maintain the highest standard of professional conduct. They advise companies by providing services such as gap analysis, remediation plans, and other activities that pertain to audit preparation.
How VC3 Can Help Your Business Prepare For CMMC Compliance
Although it may seem daunting, Cybersecurity Maturity Model Certification (CMMC) does not have to be a strenuous process.
As a CMMC Registered Provider Organization (RPO), we help companies implement and maintain the controls of CMMC so they can bid on contracts with the Department of Defense and its supply chain. With over 30 years of experience helping companies with compliance requirements, so you can expect to be promptly prepared for any CMMC certification level as quickly and painlessly as possible.
The DoD recognizes that security is an utmost concern, and should never be substituted for cost, schedule, or performance. The Department is committed to keeping sensitive data safe and protecting all parties involved in the contract process.
We are committed to getting your company certified to your desired level.
