You see it in the news daily – another company has fallen victim to a cyber attack. As a business leader, you know it’s possible that a cyber attack could impact your company too, and that you need to take the necessary security precautions to keep your data safe.
Yet when you look at your cyber security stature, you might find that you’re missing some essential cyber security layers – two of which are penetration testing and vulnerability scanning.
These tests look for the holes in your network that an attacker can exploit. Both have their benefits. Which one is right for your business? Do you need both?
That’s what this article will help you figure out. We’ll cover:
- What Is a Penetration Test?
- What Is a Vulnerability Scan?
- What’s the Difference Between a Penetration Test and a Vulnerability Scan?
- How to Choose Between Penetration Testing and Vulnerability Scanning
Let’s look at the differences between these two assessment types and how to determine which is better for your business.
What Is a Penetration Test?
A penetration test, also known as a pen test, is a simulated attack on a system to identify vulnerabilities that a hacker can exploit.
Penetration tests are typically conducted by ethical hackers, also known as white hat hackers. Although they use the same techniques as malicious hackers, they perform these tests with permission, and with the goal of improving the security of your business network.
Penetration tests provide information on:
- The likelihood of an attack: How apparent and tempting of a target is your business for a cyber attack? What sort of attacks are most likely to occur?
- The feasibility of an attack: If an attacker found a potential vulnerability, how likely are they to succeed in their attempt?
- The impact of an attack: If a vulnerability is exploited, what would be the consequences?
- How best to protect against attacks: Once likely attack types and specific vulnerabilities have been identified, what countermeasures can be implemented to prevent or mitigate an attack?
Penetration tests can be conducted internally by your company’s cyber security team or by an outsourced managed security services provider (MSSP). They can be done manually or with the help of automated tools.
Some advantages of penetration tests include:
- They’re more comprehensive than vulnerability scans. Penetration tests try to break in. They assess the feasibility and likelihood of your vulnerabilities being exploited, giving you a more in-depth assessment of your cyber security hygiene.
- They can identify vulnerabilities that other methods may not detect. Some vulnerabilities can only be found by trying to exploit them. Penetration testing replicates an attack on your network, providing you with insight that other methods cannot offer.
Some problems with penetration tests include:
Penetration tests are a great way to uncover vulnerabilities in your network, but they also have their downsides.
- They can be disruptive to business operations. For example, the cyber security professional conducting your penetration test will need access to systems and networks to launch an attack.
- They can be expensive. Hiring in-house cyber security professionals or an outsourced MSSP to conduct a penetration test can be costly. Penetration tests also require the expertise of advanced hacking techniques and tools.
If you’re looking to take your business’s cyber security posture to the next level, penetration tests provide a greater level of assurance that vulnerabilities will be found and fixed before they can be exploited.
What Is a Vulnerability Scan?
A vulnerability scan systematically scans a computer system or network for known vulnerabilities. Scans can be conducted manually or automated using a variety of tools. They aim to identify any systems or applications vulnerable to attack.
Vulnerabilities can include flaws in software, hardware, or firmware that could allow an attacker to gain access, take control, or steal data.
As with penetration testing, vulnerability scans can be conducted in-house or by an outsourced MSSP.
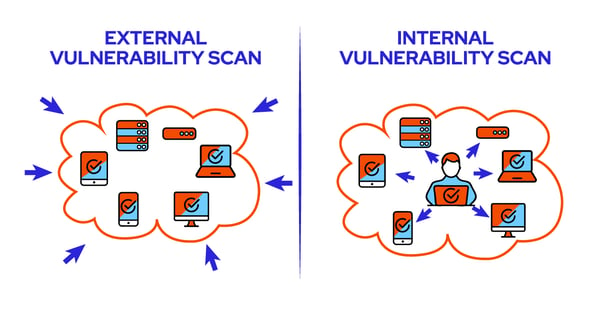
There are two types of vulnerability scans that can be performed on your business network – internal and external. They both provide you with vital information that helps you mitigate risk, but they’re not the same.
Internal vs External Vulnerability Scanning
Internal vulnerability scans are performed from inside your network to identify any systems or applications vulnerable to attack. They provide a higher-level analysis of vulnerabilities (such as outdated software and patches) and check all your endpoints for possible weaknesses.
External vulnerability scans are conducted from outside your business network and look for externally accessible weaknesses. These scans provide insights into the vulnerabilities that an attacker on the internet can exploit.
Advantages of vulnerability scanning include:
- Scans can be conducted regularly to identify new vulnerabilities.
- They can be performed quickly and easily, without interrupting business operations.
- Scan results can be used to prioritize remediation efforts.
- It’s relatively inexpensive.
Some problems with vulnerability scanning include:
- They can’t always accurately assess the feasibility or likelihood of an attack, or the potential impact on your business. This is because vulnerability scans don’t consider the specific context of a system, such as a network infrastructure or the type of data that is being protected.
- They cannot identify every vulnerability. Certain vulnerabilities may not be detectable using automated scans and may only be identifiable through manual inspection.
For these reasons, vulnerability scans are often used alongside penetration tests. By conducting both types of tests, organizations can get a complete picture of their security risks.
What’s the Difference Between a Penetration Test and a Vulnerability Scan?
A vulnerability scan identifies weaknesses; a penetration test identifies weaknesses and tries to exploit them.
These concepts can be abstract if you’re not an IT professional. Here’s a scenario that may help it come to life:
Imagine you’re walking the perimeter of your property looking for holes in the fence.
If you’re doing a vulnerability scan, you’d see a hole and make a note that you need to go fix it.
If you’re conducting a penetration test, you’d see that the hole exists and try to get through it. You’d know how attractive of an entry point it is, how feasible it is that something could get through, and what an intruder would be able to access if they succeeded.
How to Choose Between Penetration Testing and Vulnerability Scanning
So, which is better for your business – penetration testing or vulnerability scanning? The answer depends on your specific needs, security risks, and budget.
Here are a few factors to consider:
- The type of system being tested: Some systems, such as web applications, are more likely to be attacked than others. Suppose you’re responsible for the security of a system that’s likely to be targeted. In that case, you may need to conduct a penetration test to identify all potential vulnerabilities.
- The purpose of the assessment: Are you looking to identify common vulnerabilities that could be exploited by an attacker, verify that patches are being applied regularly, or get a general idea of your security posture? If so, a vulnerability scan may be the right choice. If you need a more comprehensive assessment, a penetration test may be a better option.
- The level of detail required: Vulnerability scans can provide a more general overview of your security risks, while penetration tests can provide detailed information on specific vulnerabilities.
- Your budget: Penetration tests tend to be more expensive than internal and external vulnerability scans.
- The type of data being protected: The sensitivity of the data being stored and processed can also affect the decision to conduct a penetration test or a vulnerability scan. If your data is highly sensitive, you may need to do more than just scan for vulnerabilities.
- The level of risk: Businesses face different levels of risk depending on their industry, the type of system being tested, and the data that’s being protected. If you’re responsible for the security of a high-risk system, then you may need to conduct a penetration test to identify all potential vulnerabilities.
- Your regulatory compliance or insurance requirements: Regular penetration tests or vulnerability scans may be specified to meet and maintain regulatory compliance requirements or to get better rates on cyber liability insurance.
Penetration tests and vulnerability scans are both essential tools in the fight against cyber crime. That’s why it’s not an either-or situation. We recommend companies run internal vulnerability scans monthly, external vulnerability scans quarterly, and conduct penetration tests annually.
Want to Incorporate Vulnerability Scanning or Penetration Testing Into Your Cyber Security Strategy?
Figuring out what your business needs to stay secure and compliant can be overwhelming. We’re here to help.
North America-based businesses come to us to improve their overall cyber security posture through comprehensive managed cyber security services. Contact us today for a cyber security assessment. You’ll get actionable recommendations that will guide you down the path to a secure and stable business network.


