It’s the last day of Cybersecurity Awareness Month, and today’s action step is a big one… Multi-Factor Authentication.
“Remind me what that is again…?”
Multi-Factor Authentication (also known as MFA, Two-Factor Authentication, or 2FA) is when a second verification step—your password being the first step—is required to log into an account. The most widely known MFA method is entering a single-use code sent to your verified email address or phone number.
Last week we emphasized the importance of strong passwords and now we’re talking about even more login security. If you have strong passwords, why is MFA important?
Multi-Factor Authentication blocks 99.9% of all attacks.
Imagine the front door of your house has two locks: one is a keyed lock and the other requires your fingerprint. Now imagine there’s a known criminal with an infinite number of keys going door-to-door trying each and every key. It’s a numbers game. At some point they’ll find the right key to the right door.
But now what? There’s still a second lock. And now you’ve been notified that someone has unlocked the first lock. Odds are good you’re not going to rush home from the office to scan your fingerprint and let them in. In fact, you’re probably going to change the key right away.
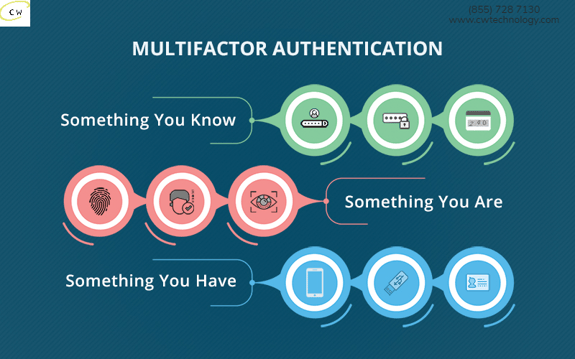
This is exactly how MFA works. There are three main types of MFA methods.
KNOWLEDGE-BASED
These are things you know. Things like answers to security questions or a secondary PIN. Be careful of using security questions that can be easily guessed or discovered (birth place, spouse’s name, etc).
POSSESSION-BASED
These are things you have. These require you to have something actively in your possession at the time of logging in. This could be access to your texts or email to receive a one-time code, generating a code from a smartphone app, or even a physical USB key or security fob.
INHERENCE-BASED
These are things you are. Things unique to you as an individual like fingerprints, voice recognition, facial recognition, or other biometrics.
Multi-Factor Authentication is continuously gaining traction and more and more services are requiring strong secondary authentication methods.
In fact, industry regulators and government agencies like the FTC are increasingly requiring MFA for certain industries and activities. We’ll be talking more about this in November, so stay tuned.
Like passwords, it’s important to have a system for keeping track of MFA methods. If you need help creating a comprehensive security plan for your business, we’re here to help as always.
Oct 31, 2022
Related Posts

Blog
|
3 Min Read
Cybersecurity Alert: Nation States Attacking and Exploiting Water Systems
The federal government recently alerted governors about nation state actors (China and Iran) currently conducting cybera...
Read More

Blog
|
3 Min Read
Can I Outsource Cybersecurity and Keep Our Internal IT Team?
Whether you know that you need outsourced security services or feel that you’ve outgrown what your internal IT team can ...
Read More

Blog
|
5 Min Read
Top 10 Tips for Choosing an Outsourced Cyber Security Company
Evaluating outsourced cyber security company services? Use these 10 talking points to see which one can deliver the resu...
Read More

