Imagine this… a piece of malicious code gets onto your computer via an unknown vulnerability in one of your programs. It starts to run a command and simultaneously sends out a communication to an IP address known to be malicious.
Both activities get stopped in their tracks by the Endpoint Detection and Response (EDR) software on your machine. The bad code is quarantined, the threat remediated, and the security team alerted. Data from the incident is collected so the team can determine what happened and prevent it from happening again.
The EDR software that saved the day in this scenario is just one piece of the security tech stack that we use here at VC3 to protect clients from cyber threats. We have many tech tools in our layered defense, and an in-depth thought process is involved in choosing each one, starting with the NIST security framework that has a cyclical approach to cybersecurity.
- NIST Framework Shapes a Comprehensive Security Strategy
- Ease of Integration and Automation
- Expertise Necessary to Manage Every Tool
- Emerging Trends and Feedback Inform Strategy
- Cyber Security is a Process, Not a Project
NIST Framework Shapes a Comprehensive Security Strategy
Using an established framework to create cyber security strategy is very important because it requires starting with the big picture. When you don’t work off a framework, it’s easy to focus on the wrong things, creating holes in your security posture. You may be able to pull the best security software off the shelf, but unless you understand where the tool fits in a layered strategy, you’re going to get a false sense of security.
You can get an idea of what the big picture we’re talking about looks like by learning about the NIST cyber security cycle.
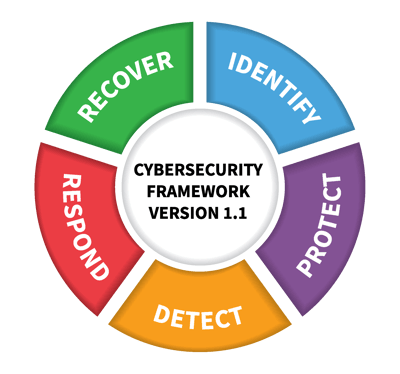 Source: NIST
Source: NIST
1. Identify – What you are protecting.
2. Protect – Tactics used to prevent attacks.
3. Detect – Tactics used to identify intruders.
4. Respond – Tactics used to stop intruders.
5. Recover – Plan for how you’ll resume normal operations after stopping an intruder.
Ease of Integration and Automation
The ease with which you can integrate security tools together has great implications for managing the whole cyber security cycle. For example, if and when an intruder event occurs, you want your EDR to be able to push data to other software tools that receive information from different sources.
There are usually many moving pieces involved with responding to an intruder event, and gathering data from different tools is how you determine exactly what happened. While much of this process is automated, the security team’s expertise ultimately puts all the pieces of the event puzzle together.
Expertise Necessary to Manage Every Tool
Of all the people that VC3 clients have working for them, the cyber security team is probably the one they see the least. Unless an individual is unfortunate enough to click on a phishing email and find their computer locked up, the security team’s work is totally behind the scenes.
If you could look over their shoulder, you’d see these cyber security specialists involved in a variety of activities throughout the day. Each tech tool requires management, and they all have alerts that need attention from time to time.
Emerging Trends and Feedback Inform Strategy
Staying up to date with what’s happening in the security and threat landscape is ongoing. The security team meets often to share what they’ve learned and make decisions on what actions if any, should be taken. Additionally, the security team keeps the rest of the company apprised of important news in the cyber security world and passes on communications that need to be shared with clients.
Clients’ perspectives on cyber security measures are very important to the team. While you can’t avoid some of the inconveniences that come with cyber security procedures – like adding another step to the login process with multi-factor authentication (MFA) – the team is sensitive to the fact that security measures won’t work if they’re not used. So there’s a continual feedback process that plays a part in evolving security strategy.
Cyber Security is a Process, Not a Project
Did you notice that the diagram of the NIST five functions is a circle? Because cyber security is a continuing process, all the layers included in the strategy are under continual review, including the technical tools. The thought process that is used to create the tech stack is dynamic. Nothing is set in stone except the end goal to secure data and access to IT systems.
Comprehensive Cyber Security Services for California Businesses
Here at VC3, we create cyber security strategy for clients that meets their individual goals for security and compliance.
While there are many decisions that business leaders need to make as we collaborate to create their strategy, creating a security tech stack isn’t one of them. If you’re ready for managed security services from a partner you can trust to bring you the information and technology you need to stand up a firm defense, get in touch.
Schedule a security assessment to reveal your security gaps today.


