2021 brought some form of normalcy back to the Southern California business climate and, if you’re like many business leaders, you’re happy to turn the calendar to 2022 with the hope that forward progress continues.
Whatever your business goals look like for the new year, they’ll need to be supported by a solid business technology plan.
We may still be facing the challenges that come with a pandemic – supply chain issues, the Great Resignation, and increasing cyber attacks, to name a few – which makes planning and budgeting even more important in 2022. How you plan for technology will affect your ability to meet your goals and pivot with changing circumstances.
Whether you’ve been creating business technology plans for years or you’re creating your first one today, here are a few things we can already see coming that need to be planned and budgeted for in 2022 (if you haven’t taken care of them already).
- Optimize Remote Workers
- Comply with NIST and CMMC Cyber Security Regulations
- Secure Your Network with Endpoint Detection and Response (EDR)
- Enable Multi-factor Authentication (MFA)
- Conduct a Third-party Cyber Security Assessment
- Cultivate Cyber Security Responsibility
- Prepare for Microsoft Office 365 Price Increases
- Review Your Backup Strategy
- Replace On-Premises Microsoft Exchange Server
Let’s take a look at nine essentials to include in your 2022 business technology plan.
Support Your Goals and Avoid Surprises with a Business Technology Plan
1. Optimize Remote Workers
The pandemic changed attitudes about remote work. Companies that never thought they would have remote workers pivoted towards work-from-home as a long-term arrangement. However, data visibility and data integrity are concerns, whether those remote workers use corporate or personal devices.
If you haven’t done so already, make sure that you have data access policies in place that detail how employees should retrieve and save data. You also need to ensure your remote workers are following policies to keep data visible to IT so that it can be managed and backed up.
That means that policies are taught and enforced, but you also provide employees with the technology they need – like VPN access and fast connectivity – to follow your guidelines.
This also brings up the conversation of company-owned and managed devices versus employees using their personal computers for work. Many companies had employees use their personal computers out of necessity at the beginning of the pandemic. It may be time to revisit that conversation.
- Are your employees’ computers and networks secured to the standard you require?
- Did you send company-owned computers home with employees?
- Are they being managed effectively?
Remote working can be great for both your organization and people, but it comes with security risks that cyber criminals are actively exploiting. It’s time to address those.
2. Comply with NIST and CMMC Cyber Security Regulations
If you’re in a government supply chain, you need to become familiar with NIST or CMMC compliance if you aren’t already.
NIST (National Institute of Standards and Technology) is a set of frequently updated guidelines designed to improve cyber security standards among government contractors.
Even though most of the government’s sensitive information is classified, vendors still use a large chunk of unclassified data to meet their contractual obligations. NIST 800-171 compliance not only protects this information but also safeguards your proprietary data.
CMMC (Cybersecurity Maturity Model Certification), on the other hand, is for organizations that have dealings with the Department of Defense (DoD). This certification is valid for three years and verifies your ability to protect unclassified government information.
The requirements and certification levels have evolved since CMMC was first announced. According to the most recent CMMC 2.0 guidance, there are three certification levels based on the maturity of your cyber security practices.
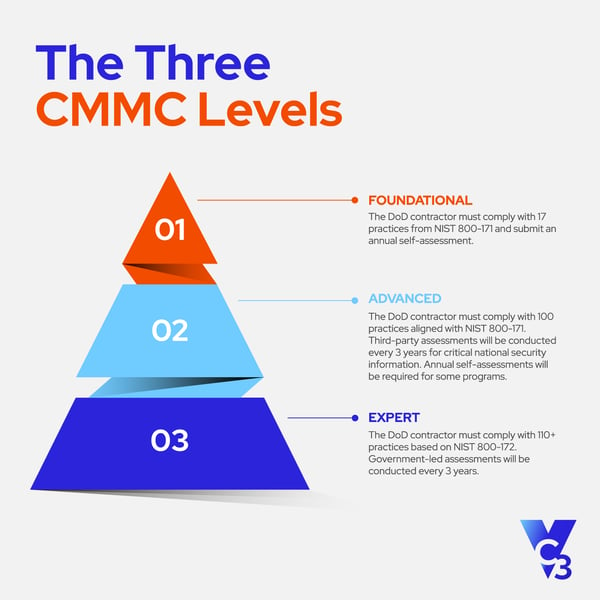
Compliance standards can be complex, but what it really comes down to are good cyber security and data hygiene practices.
When performing a NIST gap analysis or a CMMC audit readiness assessment, we find that our managed IT services clients typically already meet 70-80% of the technical control policies since they’re part of our recommended standard practices. However, not all of the controls are technical, so there can still be quite a bit of work to be done to meet compliance in many cases.
3. Secure Your Network with Endpoint Detection and Response (EDR)
The coronavirus has accelerated cyber attacks, and according to BitDefender, 60% of emails in May and June of 2020 were fraudulent. These attacks are becoming more frequent, and vigilant cyber defenses are vital.
Basic firewalls and filters are no longer enough to defend against attackers using Artificial Intelligence (AI) to make their attacks faster and more targeted. The only way to fight AI is with AI, so having advanced security tools that include Endpoint Detection and Response (EDR) capabilities is essential.
EDR uses AI to determine normal traffic patterns on your servers. Then, when suspicious activity is detected, it stops it from infiltrating your network.
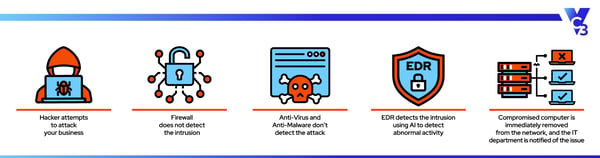
For example, suppose one of your employees’ computers is accidentally infected with malware. In that case, the EDR system will notice that the file doesn’t fit the usual traffic pattern and will block that threat from doing any damage.
EDR catches attacks that can slip past antivirus and other security layers.
We put in as many security layers as we can to prevent attacks from happening in the first place. But security is an uphill battle, with cyber criminals working just as hard to break through those layers. That’s why also focusing on detecting threats is critical.
4. Enable Multi-factor Authentication (MFA)
The 2020 Verizon Data Breach Investigations Report revealed that 80% of all data breaches resulted from weak or lost passwords. Cyber criminals may be crafty, but multi-factor authentication can stop many attacks in their tracks.
Humans are the weakest link when it comes to cyber security. That is why cyber criminals continue to use social engineering to get people to divulge their usernames and passwords.
Multi-factor authentication (MFA) requires you to verify your identity before accessing a system. For example, logging in to your email requires you to authenticate your identity using a one-time code or push notification, in addition to your regular login details.

MFA works because the hacker can’t replicate the authenticator. If you have MFA available, but you don’t use it, a hacker may enable it after taking control of your account, and then it will be a lot more difficult, if not impossible, to take back control.
5. Conduct a Third-Party Cyber Security Assessment
Cyber attacks are increasing, and every business is a target (regardless of size or industry). Prevention is a lot less painful than dealing with the impact of an attack, so you need to know if there are holes in your network and how cyber criminals might exploit them.
Not only is identifying vulnerabilities important, but you also need to be prepared to respond to a cyber incident if and when one happens.
A third-party cyber security assessment will provide you with an independent appraisal of your cyber security status. These experienced professionals know exactly what to look for and the best cyber security measures you should take to mitigate vulnerabilities that your IT team may not have the time or tools to remediate.
Remediating the issues a cyber security assessment finds will also help you get better cyber insurance coverage and lower premiums. Don't have cyber liability insurance? It's time to look into it.
6. Cultivate Cyber Security Responsibility
Your company data is the backbone of your business, and if it were to be compromised, the impact could be huge. That’s why every employee needs to understand that cyber security is a shared responsibility.
Employees will take cyber security seriously when they are educated on the value of company data, the potential impact of a cyber attack, and how to recognize and respond to a possible attack. The attitude that management takes regarding cyber security will significantly affect whether employees view cyber security as just something that’s enforced or something for which they are responsible.
Help employees understand your security expectations by training them to follow security policies. Enable employees to be savvy digital citizens by educating them about cyber criminal tactics with cyber security awareness training.
7. Prepare for Microsoft Office 365 Price Increases
Microsoft has some big changes planned for 2022. Beginning on March 1st, the cost for most Office 365 licenses will increase by 15-20%.
As of now, here are the product and price increases you can expect:
- M365 Business Basic (From $5 to $6 per user)
- M365 Business Premium (From $20 to $22 per user)
- M365 E3 (From $32 to $36 per user)
- O365 E1 (From $8 to $10 per user)
- O365 E3 (From $20 to $23 per user)
- O365 E5 (From $35 to $36 per user)
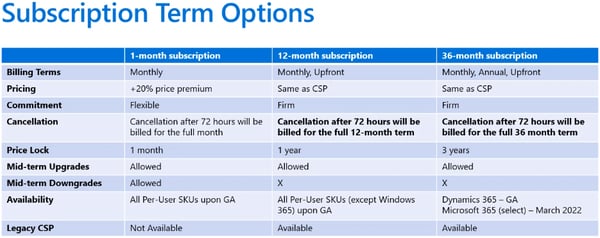
The licensing terms will be changing as well. Familiarizing yourself with them will help you budget appropriately and avoid any surprises.
For example, you used to be able to add or remove licenses on a month-to-month basis, which was very handy (especially for seasonal businesses). That won’t be the case moving forward unless you’re willing to pay a premium.
Expect Microsoft Office 365 licenses to be a one-year commitment. You’ll be able to add licenses at any time, but you won’t be able to lower your license counts like you used to. And if you want true month-to-month licenses, expect to pay a 20% premium on top of the 15% increase.
Here’s a closer look at the subscription term options:
Microsoft licensing can be complex. If you need any help figuring out what’s best for your business, we’d be glad to help. VC3 Computer Solutions is a registered CSP and can help you navigate these Microsoft changes.
8. Review Your Backup Strategy
Many companies are selective about the data they choose to backup and store offsite. After all, backups have a cost, and not all data is created equal.
However, with the prevalence and sophistication of today’s cyber attacks, it’s important to carefully review that strategy and make sure the data you consider to be mission-critical (or data that would be difficult or costly to recreate) is being backed up.
You still may ultimately decide that some data does and does not need to be backed up (or recoverable in a given time frame) but confirming that strategy annually at the least ensures that you won’t be surprised when those backups are needed.
9. Replace On-Premises Microsoft Exchange Server
It’s getting riskier to keep an Exchange Server in-house. The Hafnium cyber attack from March 2021 is an example of these vulnerabilities.
In fact, many cyber insurance carriers will not provide coverage (or it will be cost-prohibitive) for companies that have an on-premises Exchange Server.
Some IT professionals are speculating that Microsoft will not release another version of on-premises Exchange for small and middle-market businesses. Planning for that transition ahead of time will save potential headaches down the road.
Southern California IT Consulting for Creating Your Business Technology Plan
At VC3, we provide our clients with the IT guidance they need to create a business technology plan that supports organizational goals and manages the risk of cyber attacks.
If you’re not confident in your technology strategy, take the first step towards strategic IT and schedule a FREE IT assessment.


